Step 5 of 36 (14% complete)
Roles, Permissions and Product Access
Roles, Permissions and Product Access
Optimizely Identity provides a flexible framework for managing user roles, permissions, and product access across the Optimizely One ecosystem.
Role-Based Access Control (RBAC)
At the core of Optimizely Identity is Role-Based Access Control (RBAC). This allows you to define roles that group together specific permissions, making it easy to assign access based on job functions or responsibilities.
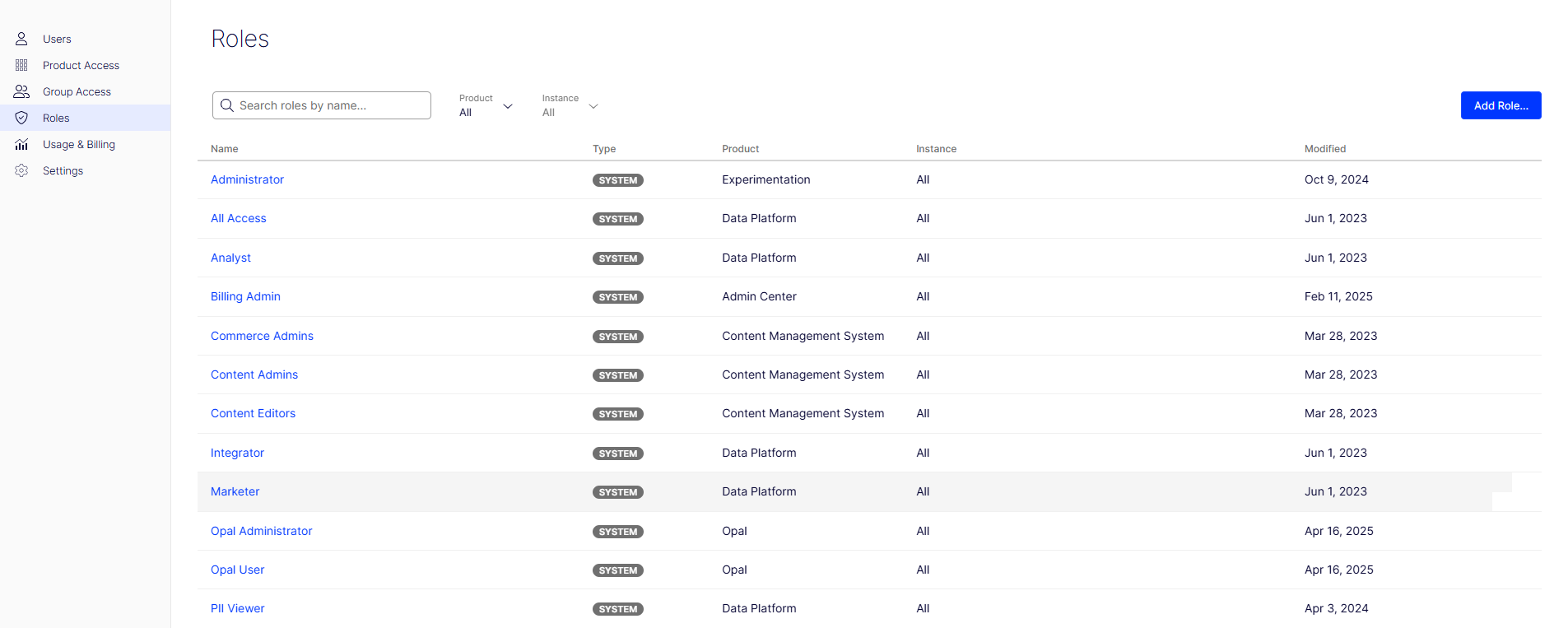
Predefined Roles
Optimizely provides several predefined roles that cover common use cases:
- Super Admin: Full access to all products and settings.
- Content Editor: Can create and manage content but not change settings.
- Viewer: Read-only access to content and reports.
- Analyst: Access to data and analytics tools.
These roles can be customised or extended to fit your organisation's specific needs.
For a full list of built in roles please refer to the official documentation here: https://support.optimizely.com/hc/en-us/articles/15858154659853-Manage-roles-and-permissions
Custom Roles
You can also create custom roles with granular permissions tailored to your workflows. For example, you might have a role for "Marketing Manager" that combines content creation permissions with access to analytics dashboards.
Product-Level Access
In addition to role-based permissions, Optimizely Identity allows you to control access at the product level. This means you can assign users or groups to specific products within the Optimizely One suite, such as CMS, Commerce, Experimentation, or Data Platform.
This flexibility ensures that users only see and interact with the tools relevant to their work, reducing complexity and improving security.
Group Management
Optimizely Identity also supports group management, allowing you to organise users into logical groups (e.g., by department or team). You can then assign roles and product access to these groups, simplifying administration as your organisation grows. Group access can be mapped to groups or policies within your IDP, enabling users to automatically join the appropriate groups when they log in - a concept known as Just In Time (JIT) provisioning. This creates a single place to manage user permissions at the IDP level, though it's worth noting that when users are removed from groups via the IDP, this change is not automatically synchronized in Optimizely Identity, although this is expected to be a feature in the future.
Benefits of RBAC in Optimizely Identity
- Simplified User Management: Easily assign and manage access based on roles rather than individual users.
- Enhanced Security: Limit access to sensitive data and tools based on job function.
- Scalability: Quickly onboard new users with predefined roles or custom configurations.
- Compliance: Maintain clear audit trails of who has access to what, supporting regulatory requirements.
Have questions? I'm here to help!
